Hosted Payment Solution
Background: As many news stories have outlined, and from what we have been seeing before, during and now after the pandemic, there has been a large uptick in malicious actors working to take advantage of the situation. The tactics employed have been wide and varied, ranging from bot attacks to denial-of-service attacks, website probing, card testing, fraud/chargebacks and increasing hacking activity. Most serious for our company and our customers has been the increased hacking activity targeting access and recording credit card payment form entries.
As we have seen over the years, the hacking of Target, Facebook, Equifax, Colonial Pipeline, Microsoft and many more as listed here https://www.upguard.com/blog/biggest-data-breaches we have concluded that if these biggest companies in the world are getting hacked, then we do not have much of a chance playing defense and keeping hackers out of our systems. The good news is we have been looking at this vulnerability for the past several years and looking for possible solutions that allow us to be proactive. We have determined that if we cannot prevent hackers from compromising or abusing systems, maybe we can deter them from doing it by removing their objective, which we believe is credit card information. If they are unable to gain access to and steal credit card information, then there would be no reason to compromise or abuse our systems.
Ultimately, we determined that a ‘Hosted Checkout’ solution combined with a ‘SCA and 3DS2 implementation’ would be a dramatic step forward in combatting card testing, hacking, fraud, chargebacks, as well as shifting liability related to accepting credit cards back to payment processors and card issuers. Below is further detail on these solutions and their benefits.
Hosted Checkout
Why are ‘Hosted Payment’ forms are the best option.
‘Hosted Payment’ forms are embedded payment form pages that are hosted and serviced by third-party external credit card processing companies to process, transmit, secure and store payment information for website checkout transactions.
The benefits of a ‘Hosted Payment’ Form Solution are:
- Greater Payment Security – Third-party payment services providers specialize in data security and so they are in the best position to secure and prevent hackers from stealing private financial data. With ‘Hosted Payment’ forms you can outsource data security and protection to these companies.
- Reduced Liability Exposure - With ‘Hosted Payment’ forms, hacking is rarely successful, and in a rare situation where it is successful, the liability falls on the third-party payment services provider and not the merchant.
- Reduced PCI Compliance Requirements – When a ‘Hosted Payment’ form solution is correctly implemented, a merchant qualifies for SAQ-A PCI Compliance which is much less cumbersome than the more involved SAQ-A-EP PCI Compliance.
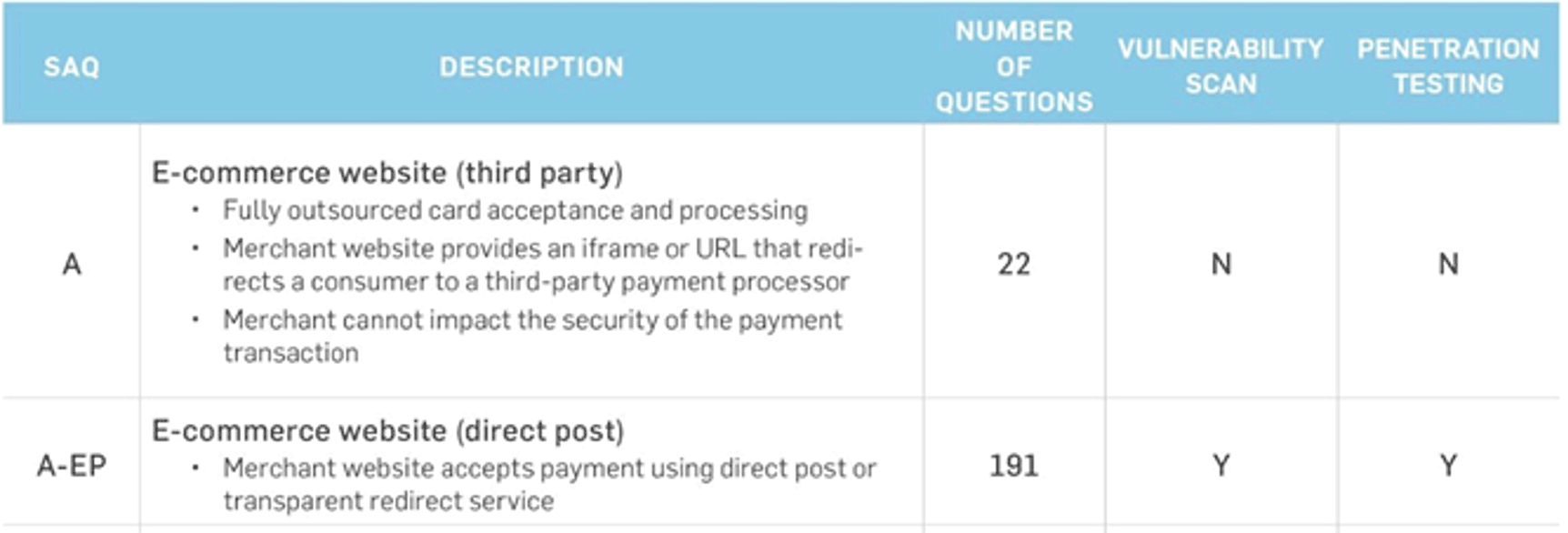
PCI Compliance Requirements
A PCI Self-Assessment Questionnaire (PCI SAQ) is a merchant’s statement of PCI compliance. It’s a way to show that you're taking the security measures needed to keep cardholder data secure at your business. As described above, when a ‘Hosted Payment’ form solution is correctly implemented, a merchant is able to qualify for SAQ-A PCI Compliance which is much less cumbersome than the more involved SAQ-A-EP PCI Compliance.
Below are the descriptions of merchants who qualify for SAQ-A vs SAQ-A-EP compliance.
- SAQ A is for e-commerce/mail/telephone-order (card-not-present) merchants that have fully outsourced all cardholder data functions. No electronic storage, processing, or transmission of any cardholder data on the merchant’s systems or premises.
- SAQ A-EP is for e-commerce-only merchants that use a third-party service provider to handle their card information and who have a website that doesn’t handle card data but could impact the security of the payment transaction. No electronic storage, processing, or transmission of any cardholder data on the merchant’s systems or premises.
Based on which SAQ level you qualify for, the below will tell you how long the PCI Compliance questionnaire (# of questions required to answer) and whether you are required to run a Vulnerability Scan and Penetration Testing.
Implementation Considerations of ‘Hosted Payment’ forms
- It is important to look into the details of how a ‘Hosted Payment’ form is implemented because some solutions are classified as ‘Hosted Payment’ forms, but they still expose the merchant to hacking, liability, and SAQ-A-EP PCI compliance. Our view is that these are NOT real solutions, and we will NOT be promoting or suggesting these options for implementation.
- It is important to understand how much design customization is permitted with ‘Hosted Payment’ forms. Because the merchant website is not in control of how the ‘Hosted Payment’ form is created or served, some solutions are fixed and cannot be changed, while others are more flexible allow you to customize the design to better match your existing website design. The amount of design customization differs greatly among these ‘Hosted Payment’ forms, and so although some solutions solve the technical and PCI requirements, their implementation looks ‘ugly’ in our opinion because the design of the form does not match the website design.
SCA and 3DS2
3-D Secure 2 (3DS2) adds a customer authorization layer in the checkout process that helps to combat card testing, fraudulent transactions, and chargebacks by shifting the responsibility for approving transactions, and liability for those approved transactions, to the customers card issuer.
What is SCA and 3DS2
On September 14, 2019, Strong Customer Authentication (SCA) requirements went into effect in Europe. The SCA requirement aims to make electronic, online and mobile payments more secure, and does so by asking customers to provide additional information to authenticate and complete their transactions. This regulation helps to verify cardholders and reduce the chance of fraudulent transactions.
Currently, when paying online, customers must enter their card number, expiration date, CVV, and postal code to make a payment. Buyers are required to complete two of the three factors of authentication when initiating a payment: something they know, something they own, and something they are.
For in-store contactless payments, SCA requirements are already met through chip and PIN requirements when certain cumulative limits are reached, or mobile wallets. Payments without this additional authentication are declined by the cardholder's bank. Payments initiated by sellers, such as recurring transactions or mail-order/telephone order (MOTO), do not require SCA.
For online card payments, the SCA requirements are met by implementing 3D-Secure 2. 3D Secure 2 (3DS2) is the new industry standard for customer authentication and is a recognized solution for meeting PSD2’s Strong Customer Authentication (SCA) requirements.
3-D Secure 2 (3DS2) stands for “Three Domain Secure V2” and is a security protocol designed to authenticate users. The three domains include the acquiring bank (merchant’s bank), issuing bank (cardholder’s bank), and the interoperability domain that supports the 3-D Secure process. 3DS offers an additional layer of security protection for card-not-present transactions. For card present payments, sellers are already not liable for fraud. The 3-D Secure 2 (3DS2) protocol was established to enable cardholders to authenticate their identity, which can help prevent the prevalence of payment fraud, hinder unauthorized transactions, and decrease chargebacks.
How does 3DS2 Work?
3D-Secure 2 (3DS2) defines a multi-factor authentication mechanism that can be used to satisfy the requirements of Strong Customer Authentication (SCA). This is either done through a challenge flow where the customer is required to provide additional information to complete their transaction, or the frictionless flow where the customer can complete their checkout without any additional steps.
- The transaction is sent through a “frictionless” flow if the issuing bank determines that enough data is provided to verify that the real cardholder is making the purchase and that the authentication process is complete without additional authentication steps. Frictionless flows require no additional steps for the customer to authenticate the payment and allow the payment to be completed without extra verification.
- The transaction is sent through a “challenge” flow if the issuing bank determines that additional proof is needed to verify that the real cardholder makes a legitimate purchase. The cardholder must complete other authentication steps, making this scenario a less frictionless process. Challenge flows include (but are not limited to): a one-time passcode sent via SMS or email, a request for biometric information such as a fingerprint scan, or the customer being redirected to their card-issuing bank’s mobile app to approve a transaction.
While 3D Secure 2 (3DS2) is not technically mandatory for the US, adding 3D Secure 2 (3DS2) can help ensure a secure checkout for your customers, protect your business against fraudulent transactions, and keep your transactions compliant with Strong Customer Authentication (SCA) requirements.
Note: The customer’s card issuer, not the merchant or payment processor, determines whether to apply a challenge flow or a frictionless flow to a transaction. If your customer is experiencing issues with a challenge flow, please ask them to contact their card issuer for support.
What does 3-D Secure 2 (3DS2) look like to my customers?
For many customers, 3D Secure 2 (3DS2) will not visibly affect them at all. If their transaction is not flagged as risky or in need of verification by the card issuing bank, then the bank will approve the payment and it will be completed as usual, without any extra verification.
However, if a payment meets the criteria to trigger 3D Secure 2 (3DS2), customers will see one of the following:
- A request for the one-time passcode sent via text message (SMS) or email.
- A request for a biometric scan (fingerprint or face ID on their phone).
- A redirection to their card-issuing bank.
Note: The card issuer (Bank of America, US Bank, Wells Fargo, etc.) determines if a payment looks suspicious and what the customer sees when a 3D Secure 2 (3DS2) verification appears on their end.
What are the benefits of using 3D Secure 2 (3DS2)?
- Better fraud protection: With 3D Secure 2 (3DS2) enabled, fraudsters have a more challenging time making fraudulent payments. Adding the extra verification makes it harder for a fraudster to make a payment because they’d have to have access to a card, as well as other personal information (e.g., phone number, face ID, fingerprint).
- Fraud chargeback protection: If a payment is 3D Secure 2 (3DS2) authenticated and verified and results in a fraud dispute, the liability for fraud chargebacks then shifts from the seller to the card-issuing bank.
